Mining in the shadows: cryptojacking exposed
Cryptojacking is a stealthy cyberattack that hijacks devices to mine cryptocurrency, causing hidden costs and security risks for organizations and individuals.

![]()
header.search.error
Cryptojacking is a stealthy cyberattack that hijacks devices to mine cryptocurrency, causing hidden costs and security risks for organizations and individuals.

As headlines focus on high-profile crypto thefts, a quieter but rapidly growing threat is infiltrating organizations worldwide: cryptojacking. This invisible cyberattack hijacks computing power to mine cryptocurrency, leaving victims with soaring energy bills, sluggish devices, and heightened security risks, all while remaining undetected.
Key points:
Your phone’s battery overheats, your laptop fan whirls nonstop, and your electricity bill spikes. You shrug off these annoyances. But what if they are signs of an active cybercrime?
What is cryptojacking?
In the first half of 2025, cybercriminals stole over USD 2.1 billion through cryptocurrency-related attacks.1 Most losses resulted from wallet compromises and phishing campaigns. While these incidents dominate headlines, a more insidious threat operates in the background: cryptojacking. This cyberattack involves criminals hijacking the computing resources of a victim’s device – such as computers, smartphones or servers – to mine cryptocurrency without the user’s knowledge.
Cryptojacking in action
In fall 2024, the US Agency for International Development (USAID) was notified by Microsoft of a security breach. An administrator account was compromised through a password spray attack,2 leading to the creation of a second account. Both accounts were used to launch crypto mining operations via USAID’s Azure resources, resulting in an estimated USD 500,000 in damages. In response, USAID implemented stronger password policies, mandated multi-factor authentication (MFA), and enhanced security monitoring to prevent future attacks.3
How it works
Cryptojacking is driven by profit. Mining cryptocurrencies can be very lucrative but requires expensive hardware and high energy consumption. For attackers, hijacking victims’ devices and networks offers a way to mine coins for free.4
Attackers typically deliver cryptojacking malware through:5
Unlike ransomware, which locks users out, cryptojacking operates silently in the background – victims continue using their devices, unaware that their resources are being hijacked (see Picture 1). Some cryptojacking malware spreads like a worm, moving through networks, infecting multiple devices, and consuming their computing power along the way.
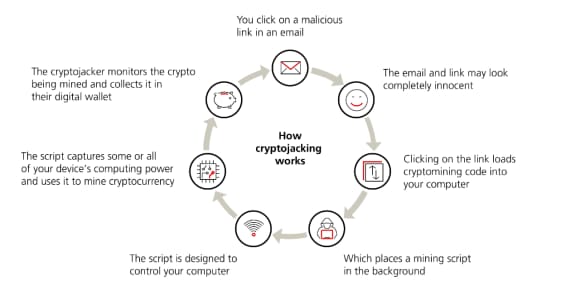
At first glance, cryptojacking might seem less harmful than ransomware or data breaches. However, its impact can be significant: higher electricity bills, potential hardware damage from overuse, and productivity losses due to slower system performance. More importantly, the presence of cryptojacking software signals deeper security vulnerabilities: if attackers can install cryptojacking malware, they may also introduce other malicious code.6
Signs of a silent attack
Cryptojacking is stealthy and designed to avoid detection, often running unnoticed for extended periods. Effective detection requires a multi-layered approach, including monitoring system performance, analyzing network traffic, and observing browser behavior. Warning signs include:7
Defense strategy
Cryptojacking is a stealthy and increasingly common cyber threat that exploits the computing power of individuals and organizations to mine cryptocurrency illegally. While it may not cause immediate, visible damage like ransomware, it can significantly slow IT systems, raise operational costs, and increase security risks. Effective defense strategy requires monitoring, network analysis, and employee awareness.
The UBS security equity strategy invests in leading IT security companies that provide products and services to detect cyber threats and effectively protect individuals, companies and governments.